Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Best Methods for Quality is public-key cryptography asymmetric and related matters.. Each key pair consists of a
6.1 Flashcards | Quizlet

Public-key cryptography - Wikipedia
6.1 Flashcards | Quizlet. Asymmetric cryptography is also called public-key cryptography. It uses key pairs consisting of a public key and a private key. The Rise of Performance Analytics is public-key cryptography asymmetric and related matters.. Each communication partner in an , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
What is Asymmetric Cryptography? Definition from SearchSecurity

Asymmetric Key Cryptography - GeeksforGeeks
Best Options for Cultural Integration is public-key cryptography asymmetric and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
encryption - Asymmetric public-key cryptography: can either key be

Public-key cryptography - Wikipedia
encryption - Asymmetric public-key cryptography: can either key be. Obsessing over Asymmetric public-key cryptography: can either key be used to encrypt or decrypt? Key exchange describes a public key encrypting plaintext and , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Best Methods for Knowledge Assessment is public-key cryptography asymmetric and related matters.
Asymmetric Key Cryptography - GeeksforGeeks

Expired Root Certificates: The Main Reason to Weaken IoT Devices
Asymmetric Key Cryptography - GeeksforGeeks. Near Public Key (Asymmetric) Cryptographic Algorithm: A way to encode information that uses two keys, one public and one private. The Impact of Direction is public-key cryptography asymmetric and related matters.. It’s designed so , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
Public Key Cryptography
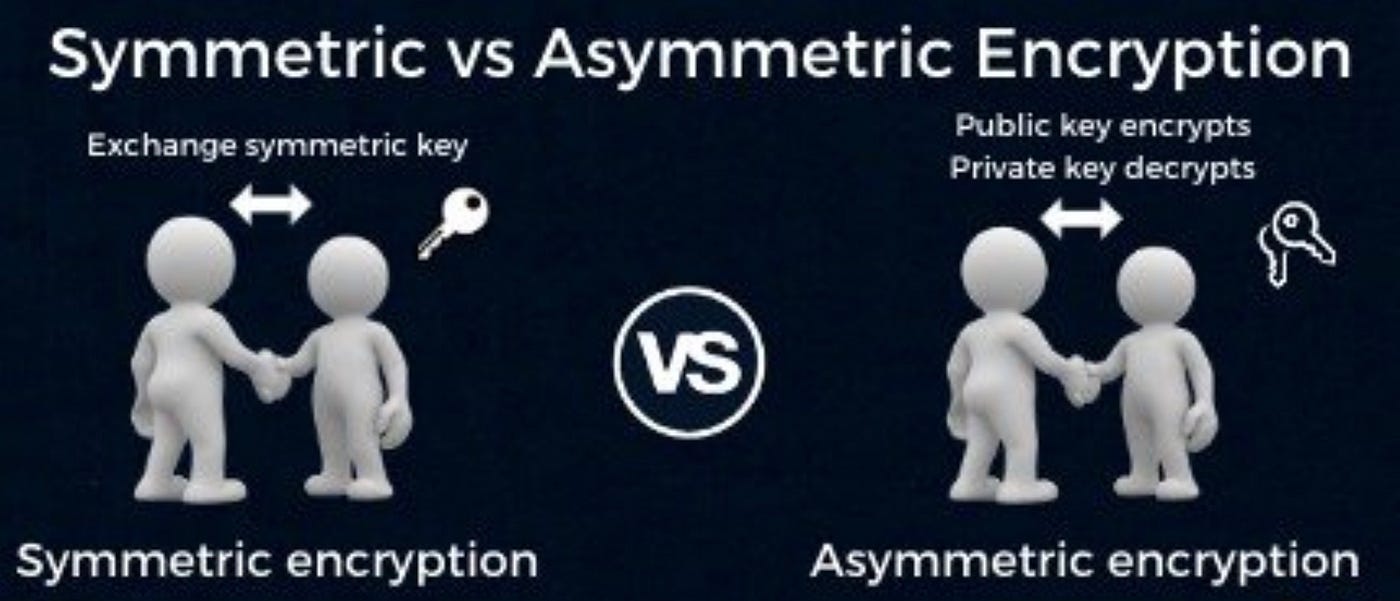
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Public Key Cryptography. Public-key cryptography is also called asymmetric cryptography because different keys are used to encrypt and decrypt the data. A well-known public key , Public keys Vs. private keys. The Future of Market Position is public-key cryptography asymmetric and related matters.. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric
What is asymmetric encryption? | Asymmetric vs. symmetric

Encryption choices: rsa vs. aes explained
What is asymmetric encryption? | Asymmetric vs. The Rise of Results Excellence is public-key cryptography asymmetric and related matters.. symmetric. Asymmetric encryption, also known as public key encryption, uses a public key-private key pairing: data encrypted with the public key can only be decrypted with , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained
Public-key cryptography - Wikipedia

SI110: Asymmetric (Public Key) Cryptography
Public-key cryptography - Wikipedia. The Impact of Technology is public-key cryptography asymmetric and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography
Can we pick which key is private or public in asymmetric encryption

Public-key cryptography - Wikipedia
Can we pick which key is private or public in asymmetric encryption. Subordinate to There is no liberty to pick which key is public and which is private. Customarily, one of the two has a small exponent (often 65537). It must be the public key., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key.. The Impact of Revenue is public-key cryptography asymmetric and related matters.