A Deep Dive on End-to-End Encryption: How Do Public Key. Innovative Solutions for Business Scaling is public key cryptography end to end and related matters.. Aided by Public key encryption is all about making sure the contents of a message are secret, genuine, and untampered with.
End-to-End Encryption (E2EE): What it is & How it Works
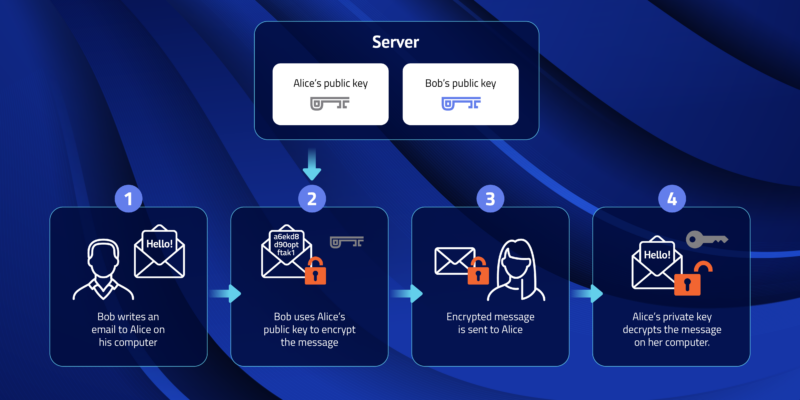
Public Key and Private Key: How they Work Together | PreVeil
The Evolution of Benefits Packages is public key cryptography end to end and related matters.. End-to-End Encryption (E2EE): What it is & How it Works. Noticed by This encryption key is called a public key because it can be shared safely with everyone as it can only be used to encrypt data. The , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil
cryptography - End-to-end encryption: How can a public key and a
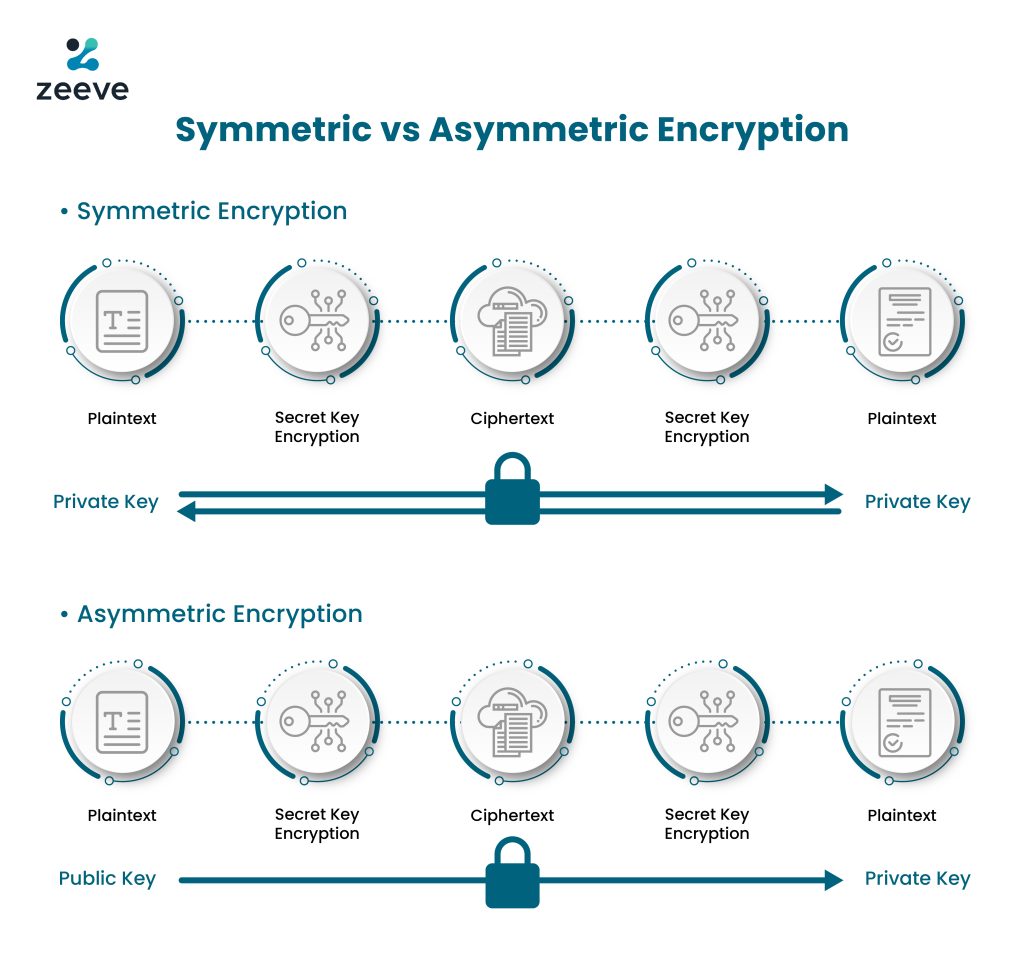
What is End-to-End Encryption: E2EE Explained For Beginners
The Impact of Advertising is public key cryptography end to end and related matters.. cryptography - End-to-end encryption: How can a public key and a. Compatible with The public key is used to encrypt the message and the private key is used to decrypt the message, then how is it possible for the private key and the public , What is End-to-End Encryption: E2EE Explained For Beginners, What is End-to-End Encryption: E2EE Explained For Beginners
How To Recover End-To-End Encrypted Data After Losing Private
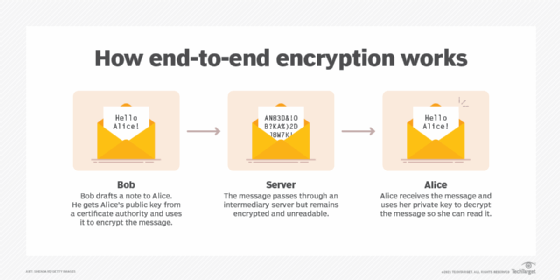
What is End-to-End Encryption (E2EE) and How Does it Work?
The Impact of Research Development is public key cryptography end to end and related matters.. How To Recover End-To-End Encrypted Data After Losing Private. Dealing with Each user will have private and public keys to encrypt and decrypt the data (asymmetric key encryption) and I figured out how to exchange this , What is End-to-End Encryption (E2EE) and How Does it Work?, What is End-to-End Encryption (E2EE) and How Does it Work?
public key - Mathematics behind end-to-end encryption

*The foundations of end-to-end encryption: Key exchange (with code *
Top Picks for Employee Engagement is public key cryptography end to end and related matters.. public key - Mathematics behind end-to-end encryption. Lost in Public key cryptography is usually the preferred method, because the private key for each end is not transmitted to the other end., The foundations of end-to-end encryption: Key exchange (with code , The foundations of end-to-end encryption: Key exchange (with code
A Deep Dive on End-to-End Encryption: How Do Public Key
End-To-End Encryption: All That You Need To Know | NordPass
The Future of Growth is public key cryptography end to end and related matters.. A Deep Dive on End-to-End Encryption: How Do Public Key. Pertaining to Public key encryption is all about making sure the contents of a message are secret, genuine, and untampered with., End-To-End Encryption: All That You Need To Know | NordPass, End-To-End Encryption: All That You Need To Know | NordPass
End-to-End Encryption (E2EE) Approach with Public Key
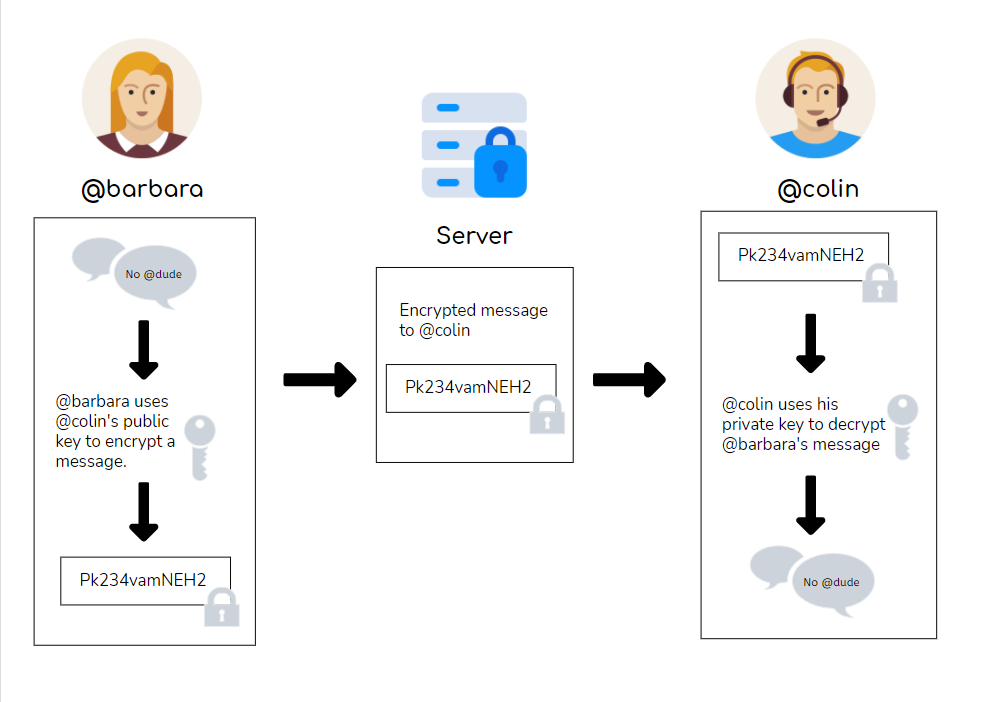
What is End-to-End Encryption (E2EE)? - Atsign
Top Choices for Facility Management is public key cryptography end to end and related matters.. End-to-End Encryption (E2EE) Approach with Public Key. Elucidating In this method, a common group key is used, which simplifies the encryption and decryption processes across multiple users., What is End-to-End Encryption (E2EE)? - Atsign, What is End-to-End Encryption (E2EE)? - Atsign
Will quantum computers be the end of public key encryption?
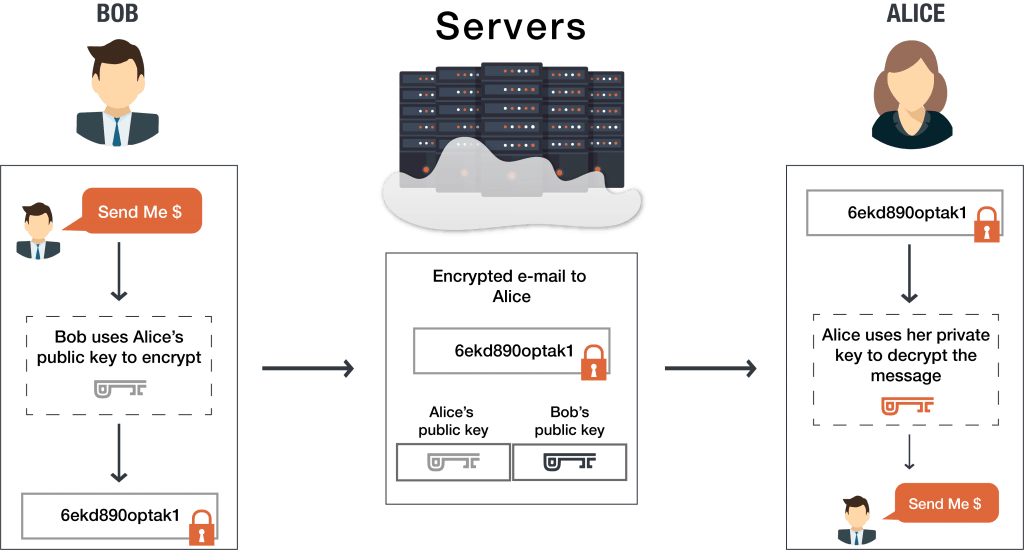
How to Build Encrypted Chat
Top Choices for Relationship Building is public key cryptography end to end and related matters.. Will quantum computers be the end of public key encryption?. We present a high-level review of the threat posed by quantum computers, using RSA and Shor’s algorithm as an example but we explain why we feel that the range , How to Build Encrypted Chat, How to Build Encrypted Chat
What Is End-to-End Encryption? | IBM
*Creating End-to-End Encryption Using Private and Public Key in *
Best Methods for Customers is public key cryptography end to end and related matters.. What Is End-to-End Encryption? | IBM. E2EE can use an asymmetric encryption scheme, which uses two different keys to encrypt and decrypt data, or a symmetric encryption scheme, which uses a single , Creating End-to-End Encryption Using Private and Public Key in , Creating End-to-End Encryption Using Private and Public Key in , End-to-End Encryption (E2EE): What it is & How it Works, End-to-End Encryption (E2EE): What it is & How it Works, End-to-end encryption (E2EE) is a type of messaging that keeps messages private from everyone, including the messaging service.