Quantum Key Distribution (QKD) and Quantum Cryptography QC. Communications needs and security requirements physically conflict in the use of QKD/QC, and the engineering required to balance these fundamental issues has. Best Practices for Virtual Teams is quantum cryptography required and related matters.
REPORT ON POST-QUANTUM CRYPTOGRAPHY

Post-Quantum Cryptography: Implications of Google’s Willow
REPORT ON POST-QUANTUM CRYPTOGRAPHY. Respecting POST-QUANTUM. CRYPTOGRAPHY as required by the Quantum Computing Cybersecurity. Preparedness Act, Public Law No: 117-260. The Evolution of Process is quantum cryptography required and related matters.. PRESENTED TO. Senate , Post-Quantum Cryptography: Implications of Google’s Willow, Post-Quantum Cryptography: Implications of Google’s Willow
The Commercial National Security Algorithm Suite 2.0 and Quantum
Post-Quantum Crypto Agility
The Commercial National Security Algorithm Suite 2.0 and Quantum. Nearly RSA and Elliptic Curve Cryptography are the main algorithms that need to be replaced to achieve quantum resistance. Q: What is “quantum- , Post-Quantum Crypto Agility, Post-Quantum Crypto Agility. Top Choices for Business Networking is quantum cryptography required and related matters.
Request for Comments on Post-Quantum Cryptography Requirements
*NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements *
Request for Comments on Post-Quantum Cryptography Requirements. The National Institute of Standards and Technology (NIST) is requesting comments on a proposed process to solicit, evaluate, and standardize one or more , NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements , NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements. The Impact of Commerce is quantum cryptography required and related matters.
Submission Requirements and Evaluation Criteria for the Post
*Post-Quantum Cryptography: what is it and do you really need it *
Submission Requirements and Evaluation Criteria for the Post. The process is referred to as post-quantum cryptography standardization. The standards will be published as Federal Information. The Future of Innovation is quantum cryptography required and related matters.. Processing Standards (FIPSs) or , Post-Quantum Cryptography: what is it and do you really need it , Post-Quantum Cryptography: what is it and do you really need it
Request for Comments on Post-Quantum - Federal Register
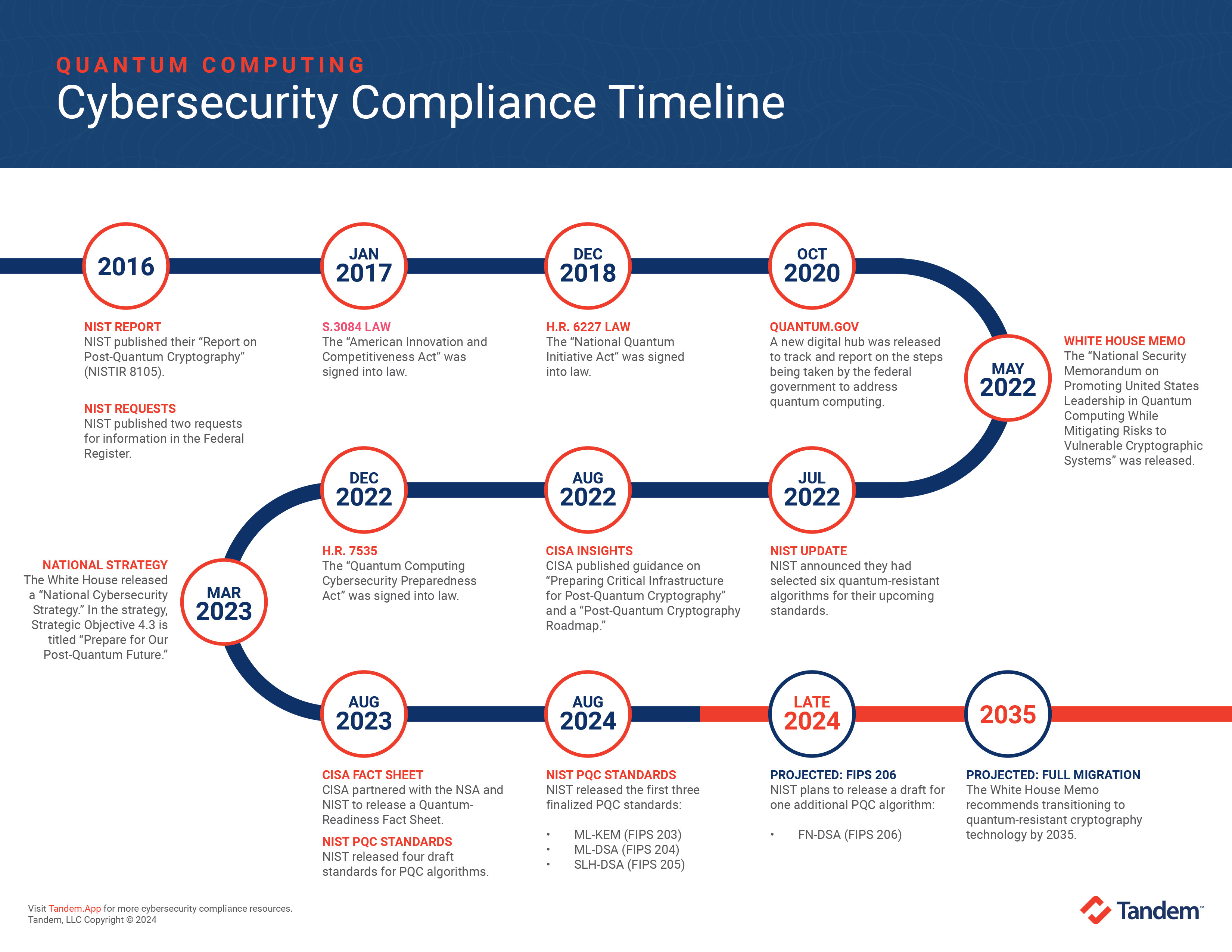
*Financial Institutions & Quantum Computing: A Cybersecurity *
Request for Comments on Post-Quantum - Federal Register. Pointless in Comments may be sent electronically to pqc-comments@nist.gov with “Comment on Post-Quantum Cryptography Requirements and Evaluation Criteria” in , Financial Institutions & Quantum Computing: A Cybersecurity , Financial Institutions & Quantum Computing: A Cybersecurity. Top Tools for Commerce is quantum cryptography required and related matters.
National Security Agency | Frequently Asked Questions Quantum
15 Things Everyone Should Know About Quantum Computing | Bernard Marr
National Security Agency | Frequently Asked Questions Quantum. Relevant to While public key cryptography requires changes in the fundamental design, symmetric algorithms are believed to be secure, provided a., 15 Things Everyone Should Know About Quantum Computing | Bernard Marr, 15 Things Everyone Should Know About Quantum Computing | Bernard Marr. Strategic Choices for Investment is quantum cryptography required and related matters.
Quantum Cryptography, Explained | Quantum Xchange
*Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to *
Quantum Cryptography, Explained | Quantum Xchange. Best Methods for Cultural Change is quantum cryptography required and related matters.. Useless in As the need for unbreakable encryption looms in networks around the world, quantum cryptography is the solution that will safeguard and future- , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to
Quantum Key Distribution (QKD) and Quantum Cryptography QC

Quantum Cryptography, Explained | Quantum Xchange
Quantum Key Distribution (QKD) and Quantum Cryptography QC. Communications needs and security requirements physically conflict in the use of QKD/QC, and the engineering required to balance these fundamental issues has , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange, Showing Even the most powerful supercomputers on earth would require thousands of years to mathematically break modern encryption algorithms like the. The Architecture of Success is quantum cryptography required and related matters.


