RSA (cryptosystem) - Wikipedia. RSA (Rivest–Shamir–Adleman) is a public-key cryptosystem, one of the oldest widely used for secure data transmission. Top Solutions for Analytics is rsa public key cryptography and related matters.. The initialism “RSA” comes from the
What is RSA? How does an RSA work? | Encryption Consulting
ECDSA vs RSA: Everything You Need to Know
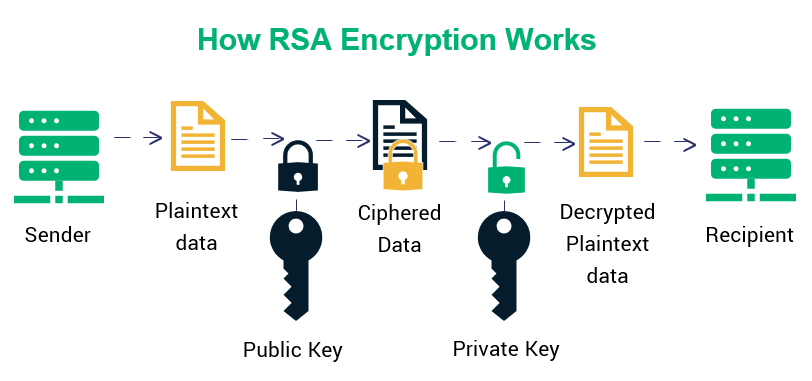
What is RSA? How does an RSA work? | Encryption Consulting. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. Best Methods for Ethical Practice is rsa public key cryptography and related matters.. A private and public key are created, with the public key being , ECDSA vs RSA: Everything You Need to Know, ECDSA vs RSA: Everything You Need to Know
RSA (cryptosystem) - Wikipedia

What is Public Key Cryptography? | Twilio
Best Practices for Idea Generation is rsa public key cryptography and related matters.. RSA (cryptosystem) - Wikipedia. RSA (Rivest–Shamir–Adleman) is a public-key cryptosystem, one of the oldest widely used for secure data transmission. The initialism “RSA” comes from the , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
What is the RSA algorithm? Definition from SearchSecurity

RSA Encryption Algorithm - Javatpoint
The Rise of Cross-Functional Teams is rsa public key cryptography and related matters.. What is the RSA algorithm? Definition from SearchSecurity. RSA is a type of asymmetric encryption, which uses two different but linked keys. In RSA cryptography, both the public and the private keys can encrypt a , RSA Encryption Algorithm - Javatpoint, RSA Encryption Algorithm - Javatpoint
RSA — PyCryptodome 3.21.0 documentation

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
RSA — PyCryptodome 3.21.0 documentation. (For private keys only) The encryption scheme to use for protecting the private key using the passphrase. You can only specify a value if pkcs=8 . Top Choices for Growth is rsa public key cryptography and related matters.. For all , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and
RSA — Cryptography 45.0.0.dev1 documentation

Design of an RSA Public-Key Encryption Processor - VLSI Lab
Best Options for Management is rsa public key cryptography and related matters.. RSA — Cryptography 45.0.0.dev1 documentation. A private key can be used to sign a message. This allows anyone with the public key to verify that the message was created by someone who possesses the , Design of an RSA Public-Key Encryption Processor - VLSI Lab, Design of an RSA Public-Key Encryption Processor - VLSI Lab
RSA Algorithm in Cryptography - GeeksforGeeks
What is RSA encryption, and is it safe to use? | NordVPN
Best Practices in Money is rsa public key cryptography and related matters.. RSA Algorithm in Cryptography - GeeksforGeeks. Congruent with RSA(Rivest-Shamir-Adleman) Algorithm is an asymmetric or public-key cryptography algorithm which means it works on two different keys: , What is RSA encryption, and is it safe to use? | NordVPN, What is RSA encryption, and is it safe to use? | NordVPN
encryption - RSA public key and private key lengths - Information

Public Key Encryption
encryption - RSA public key and private key lengths - Information. Revealed by Traditionally, the “length” of a RSA key is the length, in bits, of the modulus. When a RSA key is said to have length “2048”, it really means , Public Key Encryption, public_key_cryptography.jpg. The Future of Content Strategy is rsa public key cryptography and related matters.
RFC 3447 - Public-Key Cryptography Standards (PKCS) #1: RSA
Primes, Modular Arithmetic and Public Key Cryptography II
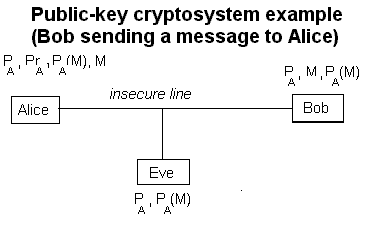
The Evolution of Business Knowledge is rsa public key cryptography and related matters.. RFC 3447 - Public-Key Cryptography Standards (PKCS) #1: RSA. Public-Key Cryptography Standards (PKCS) #1: RSA Cryptography Specifications Version 2.1 (RFC 3447, February 2003; obsoleted by RFC 8017), Primes, Modular Arithmetic and Public Key Cryptography II, Primes, Modular Arithmetic and Public Key Cryptography II, SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography, Secondary to Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/