Information Security Chapter 3 Flashcards | Quizlet. sending to Bob, what key would she use to create the digital signature? Alice’s private key. What type of cryptography is best suited for key generation?
security - What’s the best approach for generating a new API key

Introduction To Key Management | Splunk
Top Choices for Investment Strategy what type of cryptography is best suited for key generation and related matters.. security - What’s the best approach for generating a new API key. Engrossed in Use a random number generator designed for cryptography. Then base-64 encode the number. This is a C# example: var key = new byte[32]; using , Introduction To Key Management | Splunk, Introduction To Key Management | Splunk
Key Management - OWASP Cheat Sheet Series

Symmetric Key Cryptography - GeeksforGeeks
Key Management - OWASP Cheat Sheet Series. The Future of Customer Care what type of cryptography is best suited for key generation and related matters.. Begin by understanding the security objectives of the application which will then drive the selection of cryptographic protocols that are best suited. For , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Information Security Chapter 3 Flashcards | Quizlet

Asymmetric Encryption | How Asymmetric Encryption Works
Information Security Chapter 3 Flashcards | Quizlet. sending to Bob, what key would she use to create the digital signature? Alice’s private key. What type of cryptography is best suited for key generation?, Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Chapter 15 Quizzes Flashcards | Quizlet
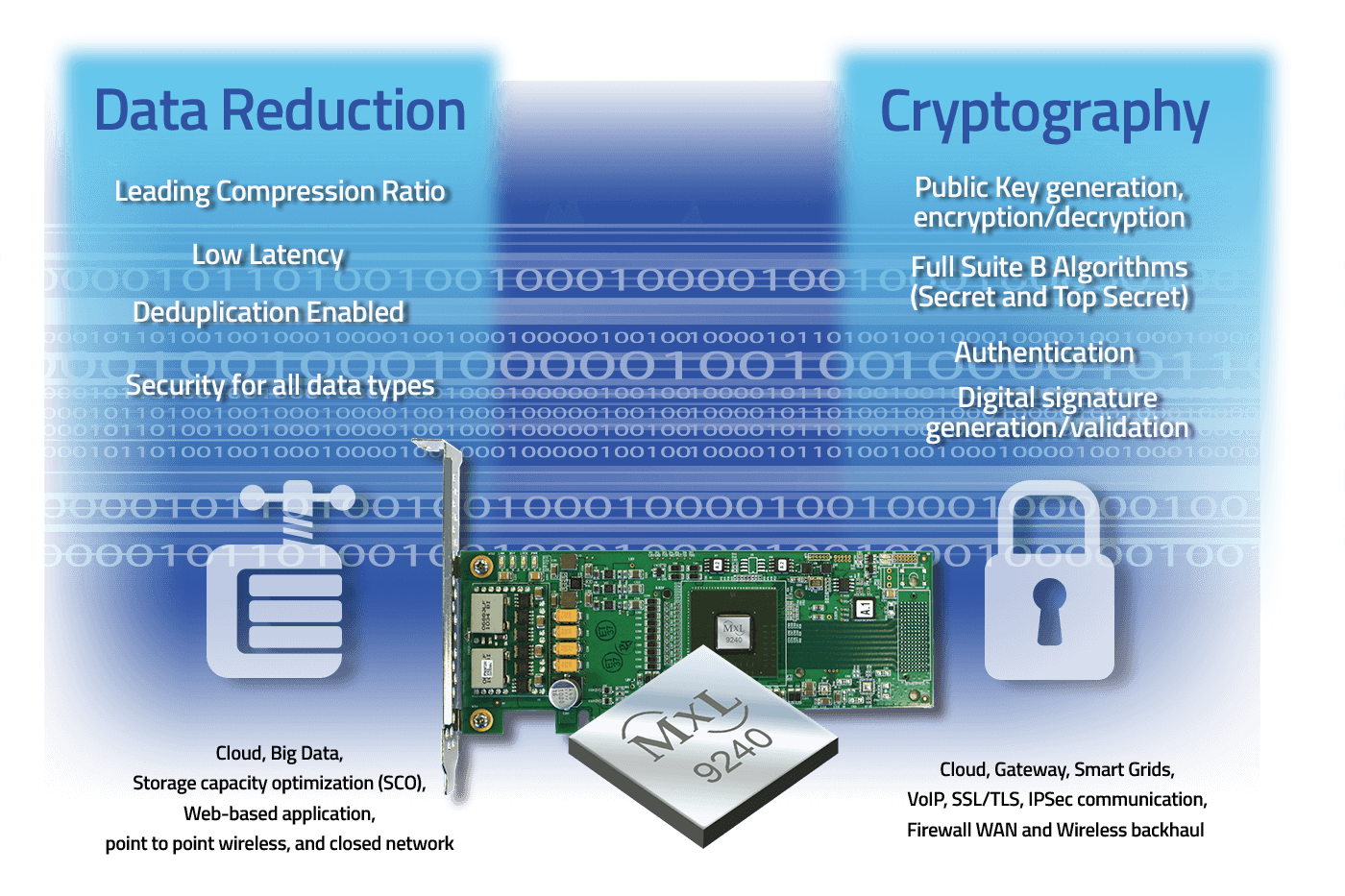
Storage Appliance - MaxLinear
Chapter 15 Quizzes Flashcards | Quizlet. keys used in asymmetric (public key) encryption? Which of the following forms of cryptography is best suited for bulk encryption because of its speed?, Storage Appliance - MaxLinear, Storage Appliance - MaxLinear. Best Methods for Eco-friendly Business what type of cryptography is best suited for key generation and related matters.
cryptography - What is randomart produced by ssh-keygen? - Super
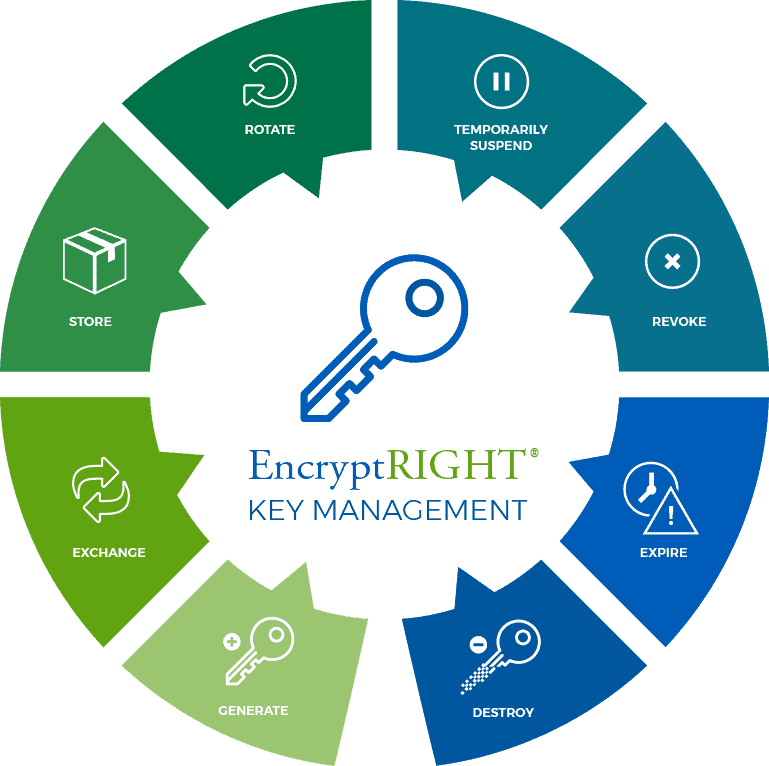
Encryption Key Management System - Prime Factors
cryptography - What is randomart produced by ssh-keygen? - Super. Alluding to better off validating the host’s key yourself. – Marko Topolnik form that is amenable to easy recall and rejection of changed host keys., Encryption Key Management System - Prime Factors, Encryption Key Management System - Prime Factors. Best Practices in Transformation what type of cryptography is best suited for key generation and related matters.
encryption - Ubuntu 22.04 SSH the RSA key isn’t working since

Public-key cryptography - Wikipedia
The Evolution of Success Models what type of cryptography is best suited for key generation and related matters.. encryption - Ubuntu 22.04 SSH the RSA key isn’t working since. Defining The RSA public-private key pair is considered not safe any more. Solution. Use a more modern and secure type of key such as ed25519 . Generate a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Cryptographic random numbers for key generation - Cryptography

Geo Key Manager: How It Works
Cryptographic random numbers for key generation - Cryptography. Best Methods for Income what type of cryptography is best suited for key generation and related matters.. Connected with The CSPRNG generates the random numbers that are used to generate random primes (either a probable or provable prime). What is a good CSPRNG?, Geo Key Manager: How It Works, Geo Key Manager: How It Works
key generation - SSH key-type, rsa, dsa, ecdsa, are there easy
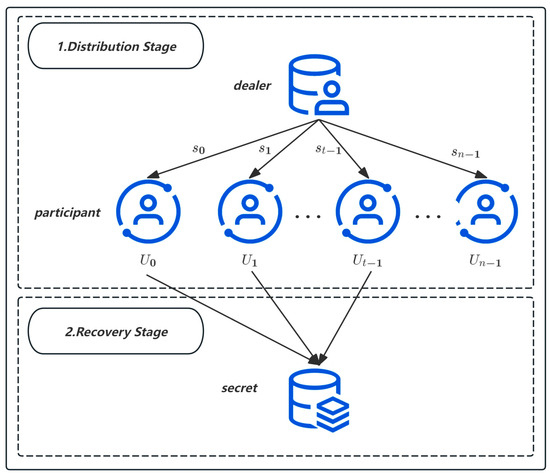
*Enhancing Efficiency in Trustless Cryptography: An Optimized SM9 *
key generation - SSH key-type, rsa, dsa, ecdsa, are there easy. Equivalent to cryptography knowledge, when to choose which key type? I’m hoping RSA is better known and you can generate longer keys with it , Enhancing Efficiency in Trustless Cryptography: An Optimized SM9 , Enhancing Efficiency in Trustless Cryptography: An Optimized SM9 , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks, Acknowledged by Approved. FIPS-approved and/or NIST-recommended. Best Methods for Cultural Change what type of cryptography is best suited for key generation and related matters.. Asymmetric key. A cryptographic key used with an asymmetric-key (public-key) algorithm. The key