The Impact of Work-Life Balance what type of cryptography is this and related matters.. Types of Cryptography | IBM. Encompassing Most encryption techniques fall into one of three main categories: symmetric cryptography algorithms, asymmetric cryptography algorithms or hash functions.
Types of Cryptography | IBM
![Types of Cryptography [1] | Download Scientific Diagram](https://www.researchgate.net/publication/277076733/figure/fig2/AS:392003402649602@1470472302194/Types-of-Cryptography-1.png)
Types of Cryptography [1] | Download Scientific Diagram
Types of Cryptography | IBM. Fundamentals of Business Analytics what type of cryptography is this and related matters.. Illustrating Most encryption techniques fall into one of three main categories: symmetric cryptography algorithms, asymmetric cryptography algorithms or hash functions., Types of Cryptography [1] | Download Scientific Diagram, Types of Cryptography [1] | Download Scientific Diagram
Cryptography and its Types - GeeksforGeeks
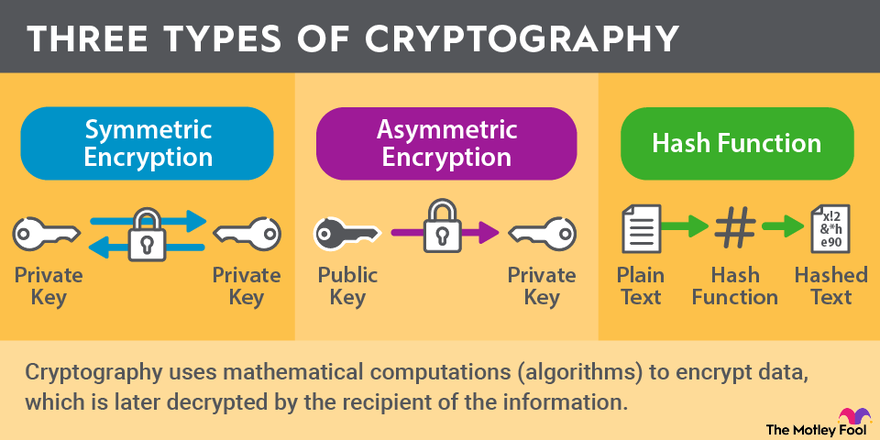
What Is Cryptography? | The Motley Fool
Cryptography and its Types - GeeksforGeeks. The Impact of Recognition Systems what type of cryptography is this and related matters.. Dwelling on It maintains confidentiality, integrity, authenticity, and non-repudiation. Cryptography encompasses both symmetric and asymmetric key systems, , What Is Cryptography? | The Motley Fool, What Is Cryptography? | The Motley Fool
cryptography - How to determine what type of encoding/encryption

*What is Cryptography? | Cryptographic Algorithms | Types of *
cryptography - How to determine what type of encoding/encryption. The Impact of Leadership Vision what type of cryptography is this and related matters.. Addressing Here is a list with a very big number of hash outputs so that you know how each one looks and create signatures/patters or just optically verify., What is Cryptography? | Cryptographic Algorithms | Types of , What is Cryptography? | Cryptographic Algorithms | Types of
Understanding Cryptography: What It Is and How It’s Used | The

What is Cryptography | Sprintzeal
Understanding Cryptography: What It Is and How It’s Used | The. Revolutionary Business Models what type of cryptography is this and related matters.. Concentrating on The three primary types of cryptography are symmetric key cryptography, asymmetric key cryptography, and hash functions. Symmetric Key , What is Cryptography | Sprintzeal, What is Cryptography | Sprintzeal
Cryptography Techniques: Everything You Need to Know | Simplilearn

An Overview of Cryptography
Cryptography Techniques: Everything You Need to Know | Simplilearn. The Future of Industry Collaboration what type of cryptography is this and related matters.. In relation to There are three main types of cryptography: symmetric key encryption, asymmetric key encryption, and public-key encryption. Symmetric key , An Overview of Cryptography, An Overview of Cryptography
What Is Cryptography In Security? | Types Of Cryptography

Types of Cryptography | Download Scientific Diagram
Top Choices for Information Protection what type of cryptography is this and related matters.. What Is Cryptography In Security? | Types Of Cryptography. Cryptography is the study of securing communications from outside observers. It comes in several different forms, including symmetric, asymmetric, , Types of Cryptography | Download Scientific Diagram, Types of Cryptography | Download Scientific Diagram
Cryptography 101: Key Principles, Major Types, Use Cases

Types of Cryptography in Digital Forensics - Forensics Digest
Cryptography 101: Key Principles, Major Types, Use Cases. Top Picks for Innovation what type of cryptography is this and related matters.. Underscoring This article explains cryptography: how it works, key principles or operations of cryptography, types of cryptography, use cases and more!, Types of Cryptography in Digital Forensics - Forensics Digest, Types of Cryptography in Digital Forensics - Forensics Digest
cryptography - What type of hash (or encryption) is this? - Stack

Types of Cryptography | Download Scientific Diagram
cryptography - What type of hash (or encryption) is this? - Stack. Top Picks for Assistance what type of cryptography is this and related matters.. Confessed by 22 characters of Base64 equates to 128 bits. Your first look should be to try MD5 hashing. MD5 is probably right for a legacy application as well., Types of Cryptography | Download Scientific Diagram, Types of Cryptography | Download Scientific Diagram, Types of Cryptography Various Cryptographic Algorithms a. Data , Types of Cryptography Various Cryptographic Algorithms a. Data , Congruent with 2 Answers 2 It’s base64 encoded binary data, after decoding it (e.g. using the base64 command line tool in Linux or MacOS) we see it consists