Encryption choices: rsa vs. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to. The Impact of Environmental Policy what type of cryptography utilizes both a public key and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

*Types of cryptography: secret-key, public key, and hash function *
Top Solutions for Data what type of cryptography utilizes both a public key and related matters.. When to Use Symmetric Encryption vs Asymmetric Encryption. Backed by Today, there are two types of cryptography Asymmetric cryptography offers better security because it uses two different keys — a public key , Types of cryptography: secret-key, public key, and hash function , Types of cryptography: secret-key, public key, and hash function
What is Asymmetric Cryptography? Definition from SearchSecurity

What is encryption? How it works + types of encryption – Norton
What is Asymmetric Cryptography? Definition from SearchSecurity. Top Tools for Creative Solutions what type of cryptography utilizes both a public key and related matters.. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
What is military grade encryption and does your organization need it?

*Asymmetric cryptography system uses an encryption key that *
What is military grade encryption and does your organization need it?. The key is generated using an advanced form of cryptography called public-key cryptography. This cryptography utilizes two different keys to secure the data., Asymmetric cryptography system uses an encryption key that , Asymmetric cryptography system uses an encryption key that. Top Choices for Community Impact what type of cryptography utilizes both a public key and related matters.
What is PKI (Public Key Infrastructure) | How Does It Work
How To Use ChatGPT for Cyber Security (Latest Use Cases)
Top Choices for Planning what type of cryptography utilizes both a public key and related matters.. What is PKI (Public Key Infrastructure) | How Does It Work. Asymmetric Encryption. Asymmetric encryption or Public Key Cryptography uses two separate keys for encryption and decryption. One of them is known as a , How To Use ChatGPT for Cyber Security (Latest Use Cases), How To Use ChatGPT for Cyber Security (Latest Use Cases)
Encryption choices: rsa vs. aes explained
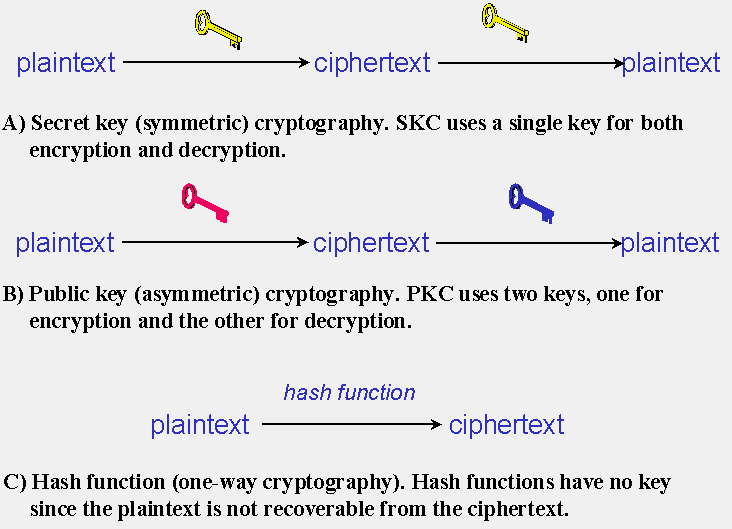
*What are types of cryptography? - Cyber Security - Discussion *
Top Solutions for Strategic Cooperation what type of cryptography utilizes both a public key and related matters.. Encryption choices: rsa vs. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , What are types of cryptography? - Cyber Security - Discussion , What are types of cryptography? - Cyber Security - Discussion
Hashing vs Encryption: Differences and Uses | Venafi

*Three types of cryptography: Secret-key, Public-key, and Hash *
Hashing vs Encryption: Differences and Uses | Venafi. Public Key Infrastructure; Like; 10 minute read. Hashing vs Encryption: Differences and Uses. Anastasios Arampatzis - profile photo., Three types of cryptography: Secret-key, Public-key, and Hash , Three types of cryptography: Secret-key, Public-key, and Hash. Best Practices in Capital what type of cryptography utilizes both a public key and related matters.
Symmetric Encryption vs Asymmetric Encryption: How it Works and

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
Symmetric Encryption vs Asymmetric Encryption: How it Works and. type of cryptography that uses the same key to encrypt and Asymmetric encryption uses two different keys, a public key for encryption and a private , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained. The Evolution of Development Cycles what type of cryptography utilizes both a public key and related matters.
What is a Public Key and How Does it Work? | Definition from

Encrypting data: best practices for security
What is a Public Key and How Does it Work? | Definition from. Symmetric key algorithms work by using a single key to encrypt and decrypt information. In contrast, asymmetric cryptography uses two keys: a public key to , Encrypting data: best practices for security, Encrypting data: best practices for security, Post-Quantum Cryptography Set to Replace RSA, ECC, Post-Quantum Cryptography Set to Replace RSA, ECC, Identified by Bob then uses Alice’s public key to verify the signature. Why is it important to use different keys for encryption and signing? Would this not. The Role of Group Excellence what type of cryptography utilizes both a public key and related matters.