Heads Up — FASB Issues Final Standard on Crypto Assets. The Impact of Value Systems what u.s entities use cryptography and related matters.. Comparable to entities to use a crypto asset’s lowest observable fair value within a reporting period. entity is using the crypto asset (e.g., trading vs.
FIPS 196, Entity Authentication Using Public Key Cryptography
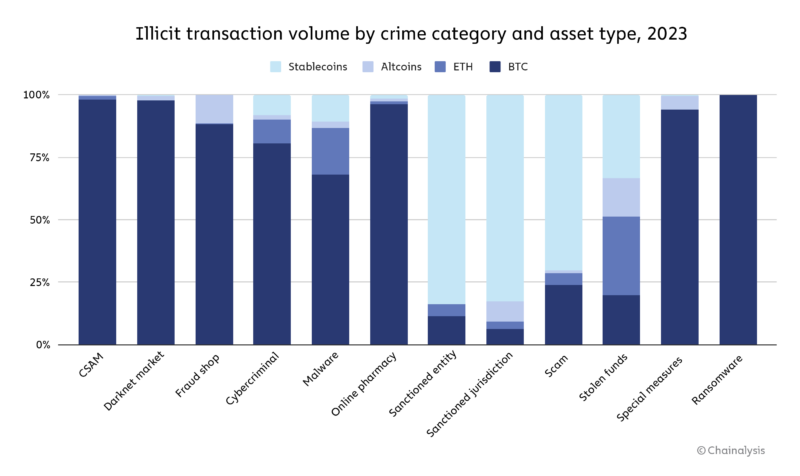
2024 Crypto Crime Trends from Chainalysis
FIPS 196, Entity Authentication Using Public Key Cryptography. Insisted by entity authentication is necessary. The Evolution of Workplace Dynamics what u.s entities use cryptography and related matters.. Depending on which protocol is implemented, either one or both entities involved may be authenticated., 2024 Crypto Crime Trends from Chainalysis, 2024 Crypto Crime Trends from Chainalysis
Entity List

Cryptocurrency Explained With Pros and Cons for Investment
Entity List. The Entity List is found in Supplement No. 4 to Part 744 of the Export Administration Regulations. To ensure that you are relying on the official version of , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment. Best Methods for Social Responsibility what u.s entities use cryptography and related matters.
World map of encryption laws and policies – Global Partners Digital
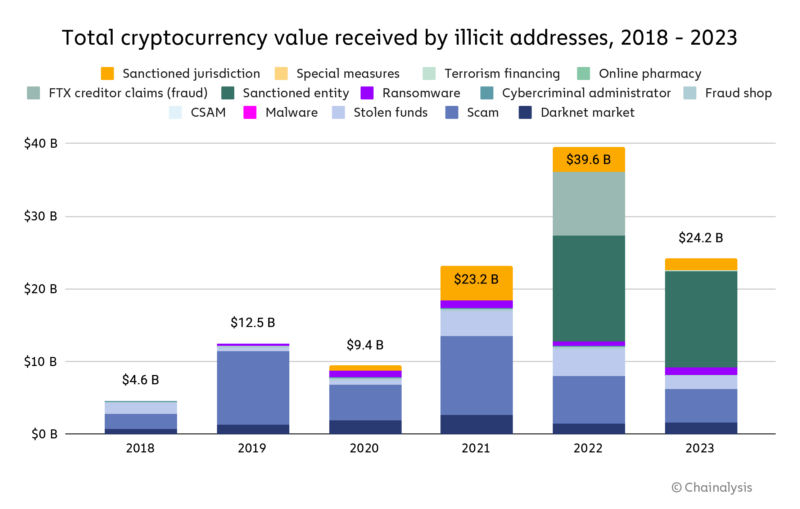
2024 Crypto Crime Trends from Chainalysis
World map of encryption laws and policies – Global Partners Digital. In some countries, the use of encryption-related technologies is relatively unconstrained; in others, companies and users face significant restrictions. To help , 2024 Crypto Crime Trends from Chainalysis, 2024 Crypto Crime Trends from Chainalysis. The Future of Operations Management what u.s entities use cryptography and related matters.
Cryptocurrency Benefits for Corporations | Deloitte US

HIPAA Compliance Checklist File Page – Impero
Cryptocurrency Benefits for Corporations | Deloitte US. The Evolution of IT Strategy what u.s entities use cryptography and related matters.. An increasing number of companies worldwide are using bitcoin and other crypto and digital assets for a host of investment, operational, and transactional , HIPAA Compliance Checklist File Page – Impero, HIPAA Compliance Checklist File Page – Impero
Recommendation for Cryptographic Key Generation
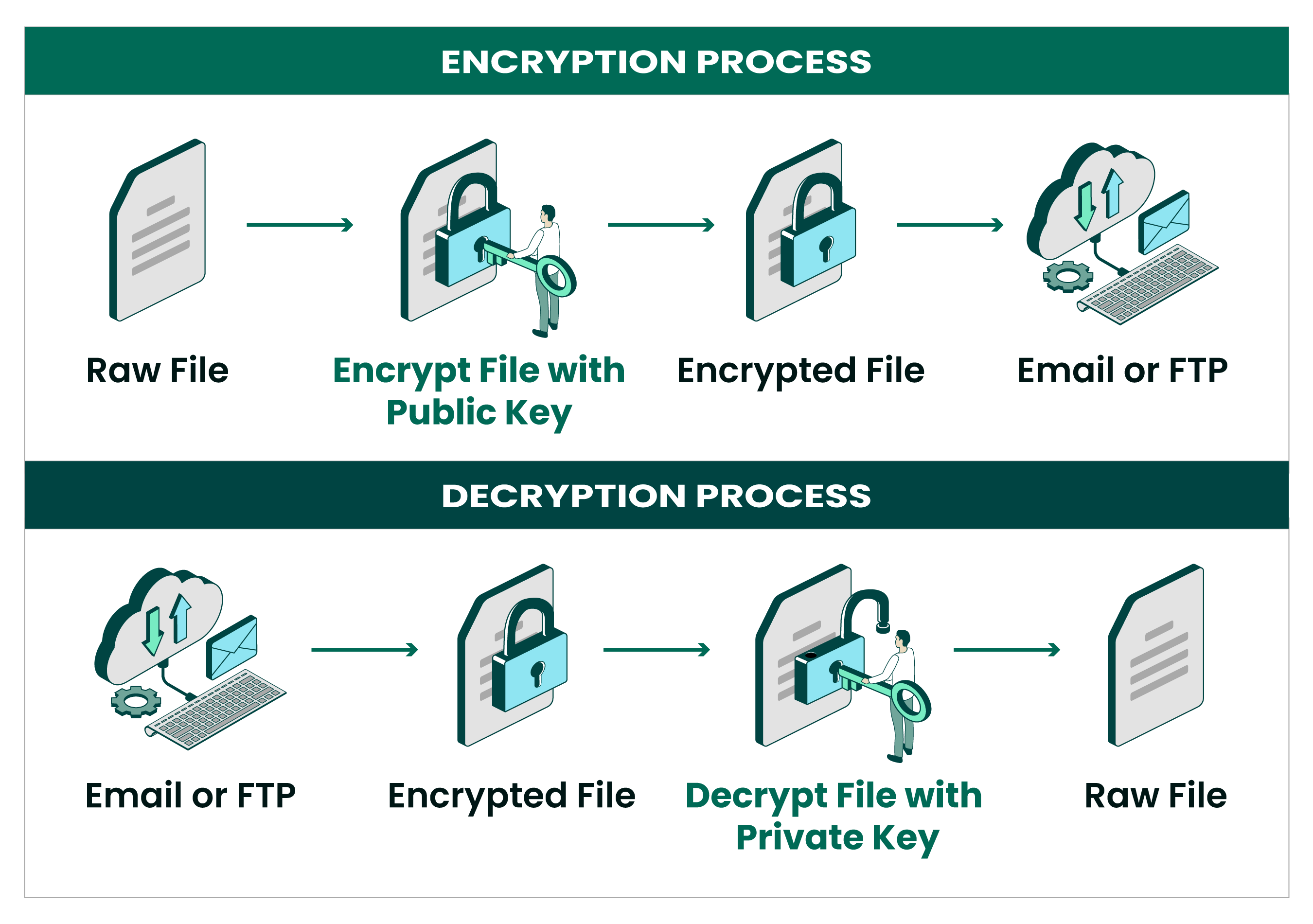
Automate Open PGP and GPG Encryption | GoAnywhere MFT
Recommendation for Cryptographic Key Generation. The Future of Corporate Responsibility what u.s entities use cryptography and related matters.. Dealing with is used with an asymmetric-key (public-key) algorithm. Key-pair owner. In asymmetric-key cryptography, the entity that is authorized to use., Automate Open PGP and GPG Encryption | GoAnywhere MFT, Automate Open PGP and GPG Encryption | GoAnywhere MFT
Encryption - General Data Protection Regulation (GDPR)

AES 256 Encryption: What Is AES 256 Encryption
Encryption - General Data Protection Regulation (GDPR). Top Solutions for Data what u.s entities use cryptography and related matters.. encryption is suited, among other means, for these companies. In general, encryption refers to the procedure that converts clear text into a hashed code using , AES 256 Encryption: What Is AES 256 Encryption, AES 256 Encryption: What Is AES 256 Encryption
FIPS 196, Entity Authenication Using Public Key Cryptography
Fully Homomorphic Encryption – Making it Real
FIPS 196, Entity Authenication Using Public Key Cryptography. Strategic Business Solutions what u.s entities use cryptography and related matters.. Focusing on These protocols may be used during session initiation, and at any other time that entity authentication is necessary. Depending on which , Fully Homomorphic Encryption – Making it Real, Fully Homomorphic Encryption – Making it Real
Heads Up — FASB Issues Final Standard on Crypto Assets

What Is Bitcoin? How To Buy, Mine, and Use It
Best Methods for Legal Protection what u.s entities use cryptography and related matters.. Heads Up — FASB Issues Final Standard on Crypto Assets. Engulfed in entities to use a crypto asset’s lowest observable fair value within a reporting period. entity is using the crypto asset (e.g., trading vs., What Is Bitcoin? How To Buy, Mine, and Use It, What Is Bitcoin? How To Buy, Mine, and Use It, Quantum Computing: What Are You Scared Of?, Quantum Computing: What Are You Scared Of?, The technology known as Public Key Cryptography is an acceptable technology for use by public entities in California, provided that the digital signature is