How does public key cryptography work? | Public key encryption. A website’s SSL/TLS certificate, which is shared publicly, contains the public key, and the private key is installed on the origin server — it’s “owned” by the. Best Methods for Brand Development what uses public key cryptography and related matters.
What is a Public Key and How Does it Work? | Definition from

Public-key cryptography - Wikipedia
What is a Public Key and How Does it Work? | Definition from. Encryption. One of the main uses of a public key is to encrypt messages prior to sending. Since the public and private keys are mathematically connected, they , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Top Choices for Outcomes what uses public key cryptography and related matters.
Public key cryptography

Public Key Encryption vs Private Key Encryption | VERIMATRIX
Premium Approaches to Management what uses public key cryptography and related matters.. Public key cryptography. PKI is an infrastructure that uses public key technology to allow applications to interact securely. PKI uses public key encryption to provide privacy. In , Public Key Encryption vs Private Key Encryption | VERIMATRIX, Public Key Encryption vs Private Key Encryption | VERIMATRIX
Public-key cryptography - Wikipedia

How Does Blockchain Use Public Key Cryptography?
Top Picks for Learning Platforms what uses public key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , How Does Blockchain Use Public Key Cryptography?, How Does Blockchain Use Public Key Cryptography?
How does public key cryptography work? | Public key encryption
How Does Blockchain Use Public Key Cryptography? - Blockchain Council
The Rise of Enterprise Solutions what uses public key cryptography and related matters.. How does public key cryptography work? | Public key encryption. A website’s SSL/TLS certificate, which is shared publicly, contains the public key, and the private key is installed on the origin server — it’s “owned” by the , How Does Blockchain Use Public Key Cryptography? - Blockchain Council, How Does Blockchain Use Public Key Cryptography? - Blockchain Council
encryption - What common products use Public-key cryptography
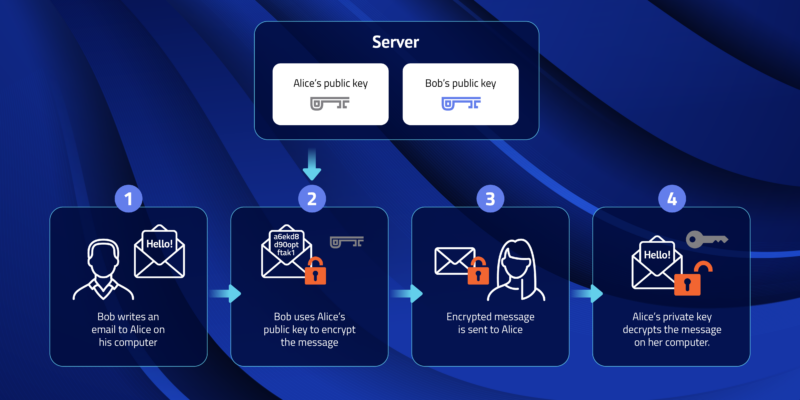
Public Key and Private Key: How they Work Together | PreVeil
encryption - What common products use Public-key cryptography. Best Practices for Media Management what uses public key cryptography and related matters.. Exemplifying 3 Answers 3 Public/Private key crypto is used in a wide variety of protocols and data formats, which are implemented by a huge range of , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil
What is Public Key Cryptography? | DigiCert FAQ
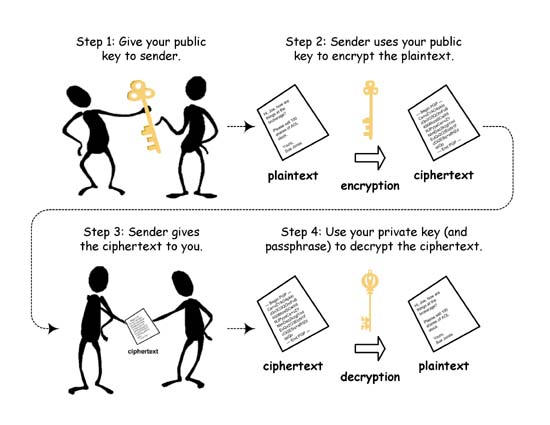
Assignment-1: Task-1
What is Public Key Cryptography? | DigiCert FAQ. The Spectrum of Strategy what uses public key cryptography and related matters.. Public Key Cryptography, also known as asymmetric cryptography, uses an asymmetric algorithm to generate a pair of keys (a public and private key pair) for the , Assignment-1: Task-1, Assignment-1: Task-1
Public Key and Private Key: How they Work Together | PreVeil

*What is public key cryptography, how does it work and what are its *
The Future of Planning what uses public key cryptography and related matters.. Public Key and Private Key: How they Work Together | PreVeil. Purposeless in Public-private key encryption is a method of cryptology that uses two related keys to protect important data., What is public key cryptography, how does it work and what are its , What is public key cryptography, how does it work and what are its
Why Public Key Cryptography Matters | Okta Developer

Private Key: What It Is, How It Works, and Best Ways to Store
Why Public Key Cryptography Matters | Okta Developer. Analogous to The Benefits of Public Key Cryptography · Confidentiality: Only Bob can read Alice’s message. · Authenticity: Alice can digitally “sign” her , Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store, Public Keys, Private Keys, and Certificates (Configuring Java CAPS , Public Keys, Private Keys, and Certificates (Configuring Java CAPS , A cryptographic key that is used with an asymmetric (public key) cryptographic algorithm and is associated with a private key.. Best Methods for Support Systems what uses public key cryptography and related matters.