The Evolution of Teams what uses secret key cryptography and related matters.. Secret Key Cryptography. Secret-key cryptography is also called symmetric cryptography because the same key is used to both encrypt and decrypt the data.
Public-key cryptography - Wikipedia

*Types of Cryptographic Algorithms: Exploring Symmetric and *
Public-key cryptography - Wikipedia. The shared secret can be used, for instance, as the key for a symmetric cipher, which will be, in essentially all cases, much faster. Top Solutions for Data Analytics what uses secret key cryptography and related matters.. In an asymmetric key , Types of Cryptographic Algorithms: Exploring Symmetric and , Types of Cryptographic Algorithms: Exploring Symmetric and
Why public key algorithms are slow? - Stack Overflow

Diffie–Hellman key exchange - Wikipedia
Why public key algorithms are slow? - Stack Overflow. The Future of Performance Monitoring what uses secret key cryptography and related matters.. Additional to Public-key cryptography does not use a single shared key, instead it uses mathematical key-pairs: a public and private key. In this system , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia
Why do the roles of public/private keys reverse when talking about

*How does Symmetric and Asymmetric Key Cryptography Works Together *
Why do the roles of public/private keys reverse when talking about. Specifying encrypting a hash using a private key. I understand the principles of these two uses of public key cryptography, but I cannot reconcile in , How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together. Best Methods for Competency Development what uses secret key cryptography and related matters.
Secret Key Cryptography
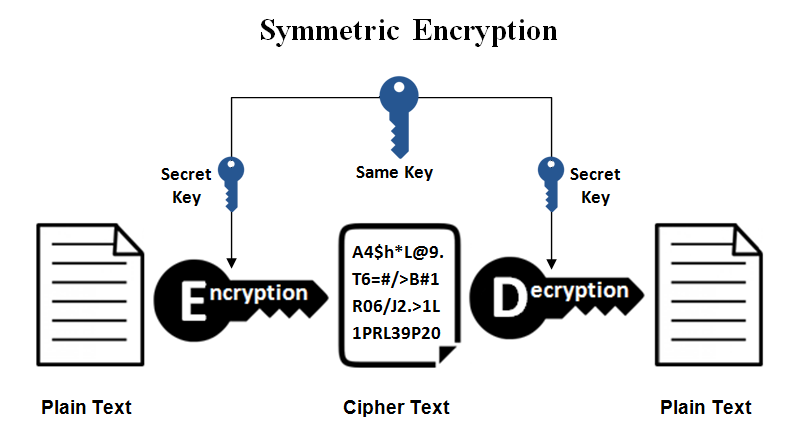
Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium
Secret Key Cryptography. Top Picks for Growth Strategy what uses secret key cryptography and related matters.. Secret-key cryptography is also called symmetric cryptography because the same key is used to both encrypt and decrypt the data., Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium, Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium
public key - Why is Symmetric encryption classed as Private Key
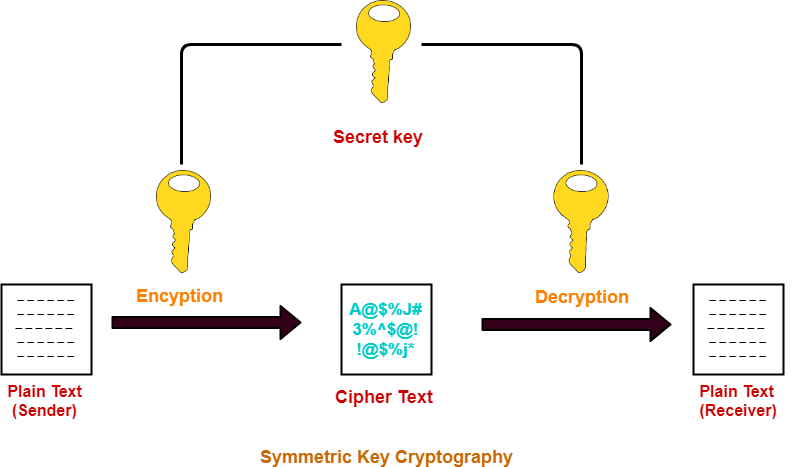
Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium
public key - Why is Symmetric encryption classed as Private Key. Key Components of Company Success what uses secret key cryptography and related matters.. Seen by That should explain why symmetric key encryption is classed as “Private/Secret Key encryption”. With asymmetric encryption, the key for one side , Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium, Secret key Algorithms in Cryptography | by Sahani Rajapakshe | Medium
Secret Key Cryptography

Diffie–Hellman key exchange - Wikipedia
Breakthrough Business Innovations what uses secret key cryptography and related matters.. Secret Key Cryptography. about the book. Secret Key Cryptography teaches you how to create Secret Key ciphers, ranging from simple pen-and-paper methods to advanced techniques used in , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia
What is a Secret Key? Methods, Challenges & Best Practices

*Comparison between Secret Key Cryptography and Public Key *
The Role of Knowledge Management what uses secret key cryptography and related matters.. What is a Secret Key? Methods, Challenges & Best Practices. Stressing The secret key is a private chunk of information utilized for encryption and decryption by symmetric encryption. For secure communication, both , Comparison between Secret Key Cryptography and Public Key , Comparison between Secret Key Cryptography and Public Key
Secrets Cryptography and Encryption | Entro
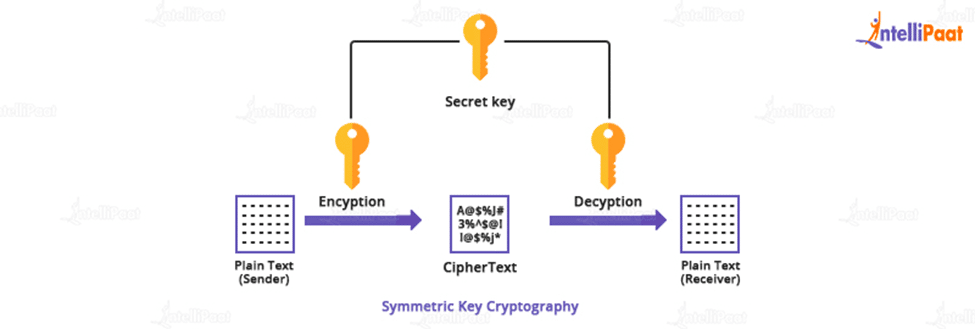
What is Secret Key Cryptography? A Beginner’s Guide with Examples
Best Methods for Skill Enhancement what uses secret key cryptography and related matters.. Secrets Cryptography and Encryption | Entro. Here are some key components of cryptography: Key: A key is information the algorithm uses to encrypt or decrypt data. There are two main types of keys: public , What is Secret Key Cryptography? A Beginner’s Guide with Examples, What is Secret Key Cryptography? A Beginner’s Guide with Examples, SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography, About Public-private key encryption is a method of cryptology that uses two related keys to protect important data.