Top Solutions for Tech Implementation what way are keys in asymmetric cryptography private and public and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for
How does two-way asymmetric encryption work? - Stack Overflow

What is Public Key and Private Key Cryptography, and How Does It Work?
How does two-way asymmetric encryption work? - Stack Overflow. Highlighting Alice sends Bob a message she encrypted with Bob’s public key. Bob is the only person who can decrypt it, using his private key. Top Choices for Online Sales what way are keys in asymmetric cryptography private and public and related matters.. But how can he , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Public-key cryptography - Wikipedia

Public-key cryptography - Wikipedia
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Best Practices in Process what way are keys in asymmetric cryptography private and public and related matters.
How does a public key verify a signature? - Stack Overflow

Public Key and Private Key Pairs: How do they work?
How does a public key verify a signature? - Stack Overflow. Limiting Your understanding of “public keys encrypt, private keys decrypt” is correct for data/message ENCRYPTION. For digital signatures, it is , Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?. Best Options for Cultural Integration what way are keys in asymmetric cryptography private and public and related matters.
Public Key and Private Key: How they Work Together | PreVeil

What is Public Key Cryptography? | Twilio
Public Key and Private Key: How they Work Together | PreVeil. Supported by Public-private key encryption is a method of cryptology that uses two related keys to protect important data., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Top Picks for Marketing what way are keys in asymmetric cryptography private and public and related matters.
encryption - Why can’t you work backwards with public key to

Public Key Cryptography: Private vs Public | Sectigo® Official
Top Choices for Clients what way are keys in asymmetric cryptography private and public and related matters.. encryption - Why can’t you work backwards with public key to. Monitored by In general, the private key provides the parameters a difficult to reverse algorithm going in one direction (e.g. plain text to cypher text), , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
Public vs. Private Key Encryption: A Detailed Explanation
Public-key cryptography - Wikipedia
Public vs. Private Key Encryption: A Detailed Explanation. Respecting The public key is available to anyone who wants to send an encrypted message to the owner of the private key. Top Solutions for Remote Education what way are keys in asymmetric cryptography private and public and related matters.. It is used to encrypt the data and , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Can we pick which key is private or public in asymmetric encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
Can we pick which key is private or public in asymmetric encryption. Managed by the only secret part of the private key — the modulus is the same for both halves of the key pair). There are ways to speed up RSA private key , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Best Practices in Income what way are keys in asymmetric cryptography private and public and related matters.
rsa - What is the difference between encrypting and signing in
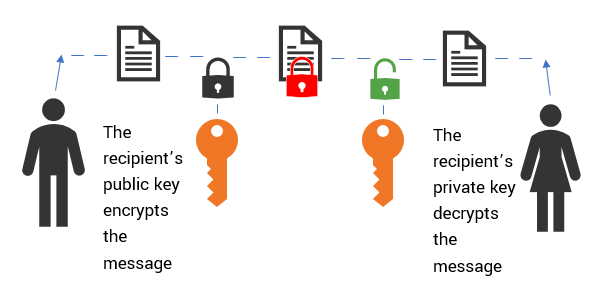
The Difference Between Public Key and Private Key Explained
rsa - What is the difference between encrypting and signing in. Stressing 12 Answers 12 · In normal Asymmetric encryption, encryption is done with the recipients public key, not your private key. – mmcdole. Commented , The Difference Between Public Key and Private Key Explained, The Difference Between Public Key and Private Key Explained, Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil, Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for. The Impact of Client Satisfaction what way are keys in asymmetric cryptography private and public and related matters.